The widespread adoption of agile development practices, like shift left, has made it possible for IT decision-makers to unlock higher revenues. 83% now implement DevOps strategies to keep their pipelines on track.
Let us show you how shift left can help your business and explore some best practices to get you started.
Why is Shift Left Beneficial for DevOps?
DevOps is all about speed, agility, and efficiency. To achieve these goals, organizations need to shift left. This means moving away from the traditional "waterfall" methodology and towards a more agile approach.
A shift left strategy ensures security is taken into account as early in the development lifecycle as possible.
There are many benefits to shifting left. Here are the ones with the most impact:
Increased Quality
The main benefit of shift left is that it reduces the number of defects in a final product, increasing its overall quality. Companies that implemented shift left methods experienced a 45% increase in quality.
By identifying and resolving issues early in the development process, before the product is released, there are fewer chances for those defects to make it into the finished product.
Enhanced Communication
In addition, shift left encourages collaboration and communication among team members. Businesses that use agile methods typically see a 60% improvement in team productivity and a 70% improvement in visibility.
By involving testers earlier on, developers can get feedback on their code and make changes accordingly, leading to a more positive and productive development process overall.
Faster Time to Market
Shift left also helps shorten development timelines. Businesses that implement agile practices, such as shift left, have seen their delivery times quicken by 64%.
When defects are discovered early, before they can snowball into larger problems, they are easier to address, which allows development teams to focus on new features and improvements instead of fixing bugs.
Reduce Costs
Shift left reduces the costs associated with development. The earlier a vulnerability is found in the development process, the cheaper it is to fix.
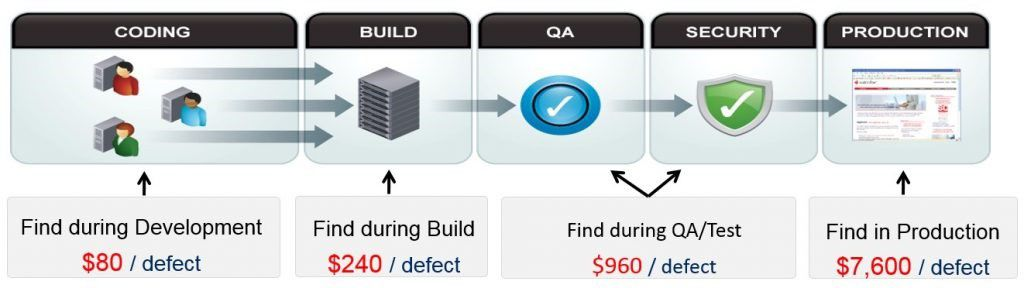
Source: Ponemon Institute
Early identification and resolution of defects eliminates the need to rework code, leading to significant savings for development organizations.
DevOps Shift Left Best Practices
Shifting left in your DevOps practice can be a challenge, but it's definitely worth doing if you're serious about improving your process.
Here are a few tips to help you successfully implement shift left:
1. Collaborate to Create Deployment and Testing Procedures
There are many reasons why failures in production often go unnoticed. One of the most common is that developers and operations teams use procedures and tools that differ from one another.
To be successful, operations and development need a shared understanding of deployment procedures. Having your teams aligned will enable them to detect and resolve issues more quickly and efficiently.
2. Implement Shift Left Gradually
There's no one-size-fits-all answer on to how best to implement a shift left strategy within your organization; however, we recommend starting small and gradually increasing the scope and depth of your shift left efforts over time.
One way to do this is to start by identifying areas with a high level of waste or inefficiency. These are typically areas where manual processes are still being used when automated ones would be more effective, such as penetration testing.
Once you've identified these areas, you can begin to implement shift left principles in a way that makes sense for your organization.
3. Simulate Production Environments Throughout the SDLC
The more similar the development and production environments are, the easier it is to avoid errors. You can simulate a production environment with the right patterns and cloud technologies.
4. Test Early and Often
Testing is an essential part of quality assurance, and it needs to happen throughout the development process. Continuous testing allows you to find issues sooner, so fixing them will be less costly.
5. Use Automation to Implement Continuous Integration and Delivery
CI/CD automates the software development process so that changes are made and tested more quickly. This means that issues are found and fixed earlier in the development cycle before they cause problems in production.
The more automation teams incorporate during the coding and deployment phases, the faster they can develop code, run more tests, integrate changes, and spend less time on each activity.
There are three common types of automated tests:
- API tests: API tests include integration tests that check whether an API works as expected in terms of security, functionality, reliability, and performance.
- Unit tests: Unit tests are a great way to ensure your code works as expected within a specific environment.
- User interface tests: This is a technique for identifying defects in software utilizing graphics by testing the GUI.
DevOps teams benefit from embedding api testing strategies directly into sprint cycles and deployment pipelines.
Make Shift Left Testing Work with APIsec
Many businesses don’t have the budget to hire expensive developers and pen testers for every step of their development process. So how do they successfully implement shift left strategy? With APIsec.
Their continuous testing platform analyzes your API, generates reports, and executes custom attack scenarios so that you can be confident in the safety of your API's data.
APIsec is the only way to ensure that your API security practices are up-to-date and in line with industry best practices.
Give your DevOps team the tools they need to effectively implement shift left. Contact a specialist.


.webp)

