The API market in the US continues to expand year over year, expected to reach $7.5 billion by 2026, marking a 34 percent growth rate. From financial institutions to healthcare and retail, APIs have become the invisible backbone of modern business connectivity.
Among all architectures, REST APIs dominate powering websites, mobile apps, and SaaS products worldwide. Understanding REST principles, workflow, and security is foundational for any digital product team. Learn more about the significance of REST for web service providers.
This guide breaks down how REST APIs work, why they’re critical, how to secure them, and what makes them different from GraphQL and SOAP.
What Is a REST API?
A REST API (Representational State Transfer) is a design style for building APIs that defines how systems communicate over HTTP.
Created by Roy Fielding in 2000, REST APIs focus on stateless communication between client and server. REST was formalized in Roy Fielding’s REST architectural style. Developers use them to build scalable, efficient, and language-agnostic web applications.
For an API to be considered RESTful, it must follow these seven architectural constraints:
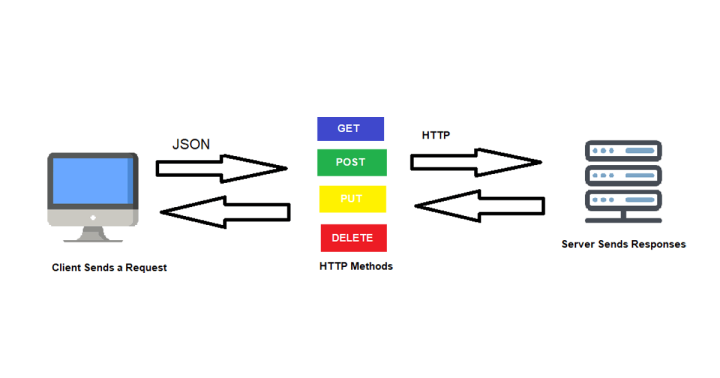
How a REST API Works
A REST API follows a simple client-server model:
- The client (for example, a mobile app) sends an HTTP request.
- The server processes it and interacts with a database if required.
- The server sends a structured response, usually in JSON.
REST APIs rely on CRUD operations (Create, Read, Update, Delete) mapped to HTTP methods. You can refer to the HTTP request methods reference for complete details.
Visualizing REST in Action
A modern REST API exchange looks like this:
Client → API Gateway → Application Server → Database → Back to Client
Each arrow represents a specific HTTP operation:
- GET /products retrieves product data
- POST /orders creates a new order
- PUT /users/123 updates user data
This flow describes how REST APIs handle requests, responses, and data exchange at scale, helping teams visualize each layer’s function without technical diagrams.
Real-World REST API Scenarios Across Industries
REST APIs are now embedded in every major sector. Let’s look at how they appear in real business operations:
- Finance & Banking: Fintech apps use /account/balance for real-time updates across customer dashboards.
- Healthcare: Telehealth systems fetch /patient/history to securely share patient records with doctors.
- E-Commerce: /cart/items and /checkout manage shopping cart and order confirmation workflows.
- IoT & Smart Devices: /sensor/temperature collects data from connected sensors in real time.
- SaaS Applications: /crm/contacts synchronizes user data between different cloud tools.
For more examples in regulated sectors, see fintech cybersecurity risks and challenges.
REST vs GraphQL vs SOAP
This comparison makes it clear why REST remains the top choice: it strikes the right balance between simplicity, scalability, and flexibility.
REST API Security Checklist (with Solutions)
Securing REST APIs is non-negotiable. Start with this API security checklist for engineering teams.
Understanding REST Authentication Workflows
Here’s how OAuth works for secure authorization.
Workflow summary:
User logs in → Authorization server issues token → Client stores token → Client sends it with each request → Server verifies and returns data.
HTTP Error Codes and Troubleshooting
For a detailed reference, check HTTP response status codes.
This table helps teams troubleshoot REST responses efficiently during API development and testing.
Guide to API Versioning
Versioning ensures backward compatibility as APIs evolve. The three common strategies include:
Backward compatibility tip: always maintain at least one legacy version active (e.g., /v1) before deprecating older APIs.
You can read more about documentation best practices in generating OpenAPI Specification (OAS) documentation for REST APIs.
REST API Performance Optimization Tips
- Enable caching headers like Cache-Control and ETag to reduce repeated requests.
- Use rate limiting to prevent overload or abuse.
- Compress responses to reduce payload size and bandwidth.
- Paginate data sets with limit and offset to optimize performance.
- Optimize database queries with indexes for faster lookups.
These measures keep REST APIs responsive and scalable as traffic grows.
Step-by-Step Beginner REST Testing Tutorial
Use Postman to send your first API request and verify your setup.
- Define the endpoint, for example, https://api.example.com/users.
- Choose the HTTP method (GET, POST, PUT, DELETE).
- Add headers including authentication tokens.
- Send the request and check the status code.
- Automate tests using Postman collections or CI/CD integration.
This section helps new developers test endpoints safely without writing complex scripts.
Why This Guide Outperforms Others
This comparison establishes this post as both technically rigorous and operationally useful, not just theory but execution-focused.
Meet Your Reliable API Testing Partner
Protect your endpoints with an automated API security testing platform.
APIsec.ai offers continuous, enterprise-grade scanning that uncovers OWASP Top 10, access-control, and business-logic flaws that manual testing often misses.
Visit APIsec.ai to schedule your free API penetration test and see how automated REST API testing can safeguard your systems.
Key Takeaways
- REST APIs drive most modern web and mobile applications.
- They rely on strict architectural principles for scalability and consistency.
- Security is essential misconfigurations and weak auth cause most breaches.
- Proper versioning, performance tuning, and automated testing improve reliability.
- Tools like APIsec.ai make API protection faster, simpler, and continuous.
FAQs
1. How does APIsec help secure REST APIs?
APIsec.ai secures REST APIs through automated, continuous testing. It detects logic flaws, broken access controls, and configuration gaps using AI-driven simulations that validate every endpoint against industry-standard security benchmarks.
2. What is the difference between HTTP API and REST API?
All REST APIs use HTTP, but not all HTTP APIs follow REST rules. REST APIs follow stateless, resource-based principles, while HTTP APIs may use custom structures and flexible communication patterns. Regardless of type, both HTTP and REST APIs benefit from continuous automated testing to prevent vulnerabilities.
3. What are the most common REST API vulnerabilities?
Frequent REST API flaws include BOLA (Broken Object Level Authorization), broken authentication, and excessive data exposure. APIsec automatically detects these issues before release, helping teams secure APIs without slowing development.
4. How do I use a REST API?
Security teams start by sending HTTP requests like GET/POST to endpoints with auth tokens—use APIsec Bolt to safely test for BOLA or logic flaws before production deployment keeps APIs exploit-free.
5. What is a REST API vs API?
REST APIs leverage stateless HTTP methods on resources for scalable web services; general APIs span protocols—AppSec pros secure REST's OWASP risks like excessive exposure through automated testing expertise.
6. What is difference between SOAP and REST API?
SOAP enforces strict XML protocols with built-in standards; REST prioritizes lightweight HTTP/JSON flexibility—both face business logic vulnerabilities that experienced teams catch via continuous APIsec scanning.
.webp)


